BloodHound Enumeration
BloodHound
Enable Sharp-Hound
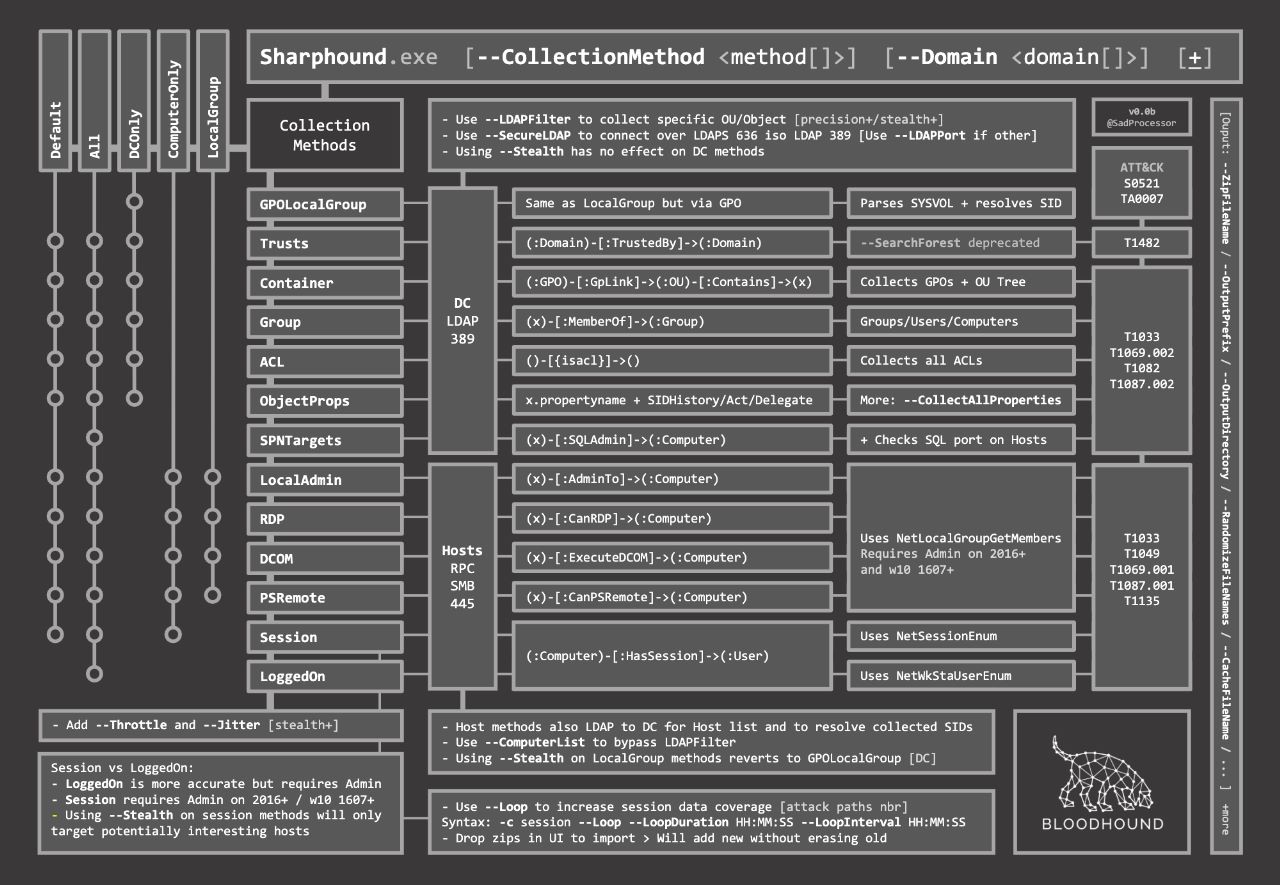
Supply data to BloodHound
The generated archive can be uploaded to the BloodHound application.
To avoid detections like ATA
Neo4j
Start neo4j and BloodHound UI on kali machine and load the zip/json files
Last updated