BloodHound Enumeration
BloodHound
Enable Sharp-Hound
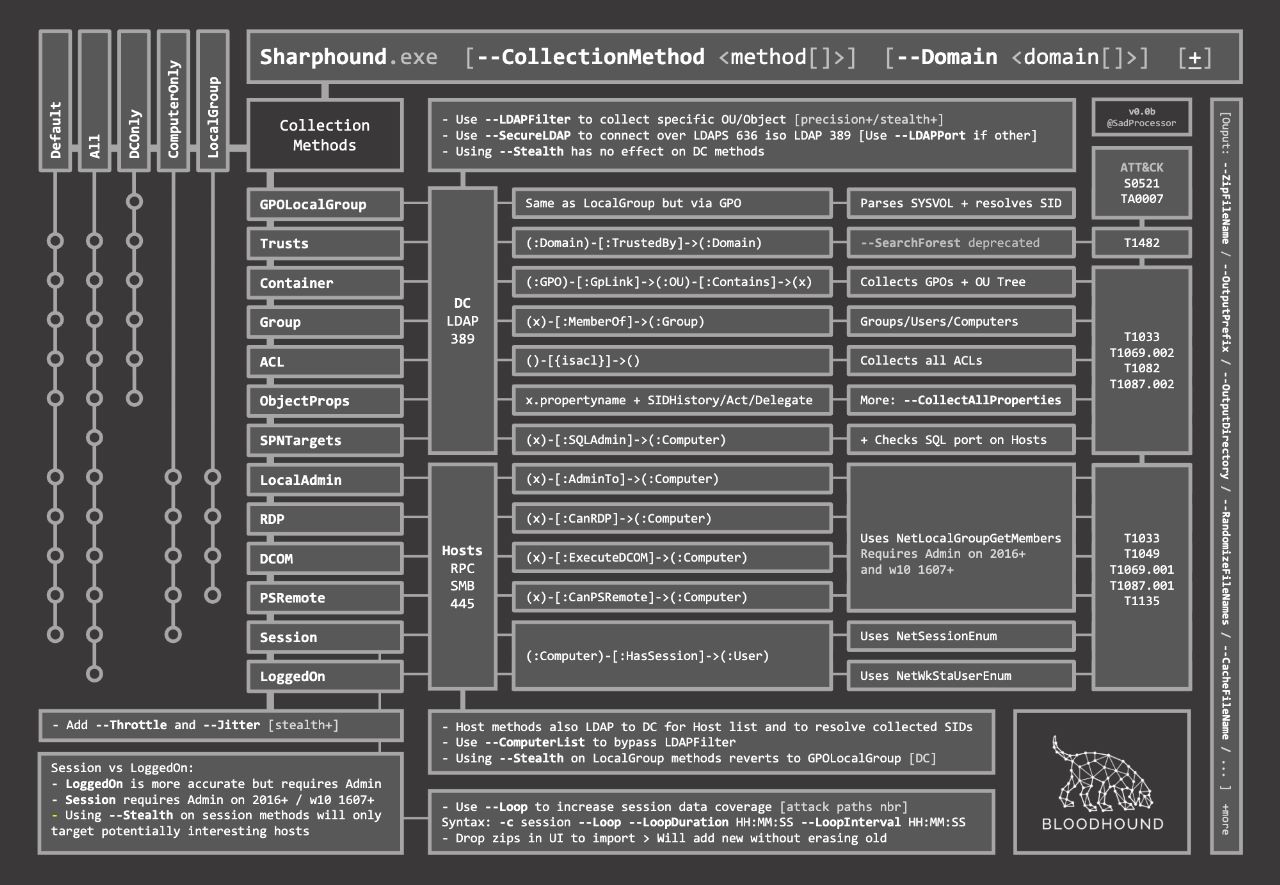
Supply data to BloodHound
The generated archive can be uploaded to the BloodHound application.
Remote BloodHound
On-Site BloodHound
To avoid detections like ATA
Neo4j
Start neo4j and BloodHound UI on kali machine and load the zip/json files
this option (Local user) unavailable on win server 2016
Last updated