adbasics_v1.2
To overcome these limitations, we can use a Windows domain. Simply put, a Windows domain is a group of users and computers under the administration of a given business. The main idea behind a domain is to centralise the administration of common components of a Windows computer network in a single repository called Active Directory (AD). The server that runs the Active Directory services is known as a Domain Controller (DC).

The main advantages of having a configured Windows domain are:
Centralised identity management: All users across the network can be configured from Active Directory with minimum effort.
Managing security policies: You can configure security policies directly from Active Directory and apply them to users and computers across the network as needed.
Note: When connecting via RDP, use THM\Administrator as the username to specify you want to log in using the user Administrator on the THM domain.
In a Windows domain, credentials are stored in a centralised repository called.
Active Directory
The server in charge of running the Active Directory services is called...
Domain Controller
Security Groups
If you are familiar with Windows, you probably know that you can define user groups to assign access rights to files or other resources to entire groups instead of single users. This allows for better manageability as you can add users to an existing group, and they will automatically inherit all of the group's privileges. Security groups are also considered security principals and, therefore, can have privileges over resources on the network.
Groups can have both users and machines as members. If needed, groups can include other groups as well.
Several groups are created by default in a domain that can be used to grant specific privileges to users. As an example, here are some of the most important groups in a domain:
Domain Admins
Users of this group have administrative privileges over the entire domain. By default, they can administer any computer on the domain, including the DCs.
Server Operators
Users in this group can administer Domain Controllers. They cannot change any administrative group memberships.
Backup Operators
Users in this group are allowed to access any file, ignoring their permissions. They are used to perform backups of data on computers.
Account Operators
Users in this group can create or modify other accounts in the domain.
Domain Users
Includes all existing user accounts in the domain.
Domain Computers
Includes all existing computers in the domain.
Domain Controllers
Includes all existing DCs on the domain.
Active Directory Users and Computers
To configure users, groups or machines in Active Directory, we need to log in to the Domain Controller and run "Active Directory Users and Computers" from the start menu:

Which group normally administrates all computers and resources in a domain?
Domain Admins
What would be the name of the machine account associated with a machine named TOM-PC?
TOM-PC$
Suppose our company creates a new department for Quality Assurance. What type of containers should we use to group all Quality Assurance users so that policies can be applied consistently to them?
Organizational Units
Managing Users in AD
Your first task as the new domain administrator is to check the existing AD OUs and users, as some recent changes have happened to the business. You have been given the following organisational chart and are expected to make changes to the AD to match it:

Note:
After the delegation enter the Phillips account by using remmina using the RDP port. Username and password: phillip: Claire2008

Inside the Phillip, account open the Command prompt and transfer it to PowerShell using Command: powershell in cmd.

Now to set the password type this command: Set-ADAccountPassword sophie -Reset -NewPassword (Read-Host -AsSecureString -Prompt ‘New Password’) -Verbose
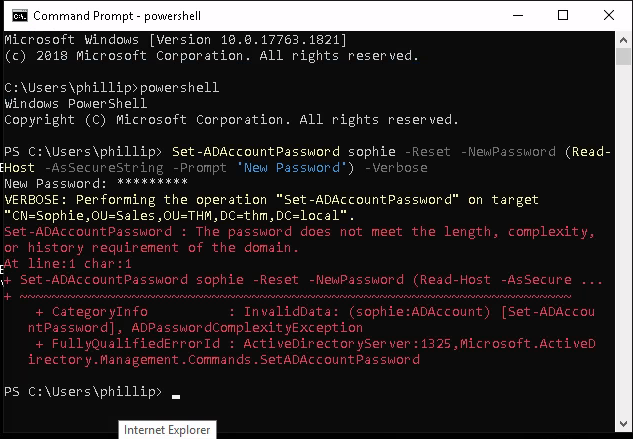
Here I have set the password: abcD12345*
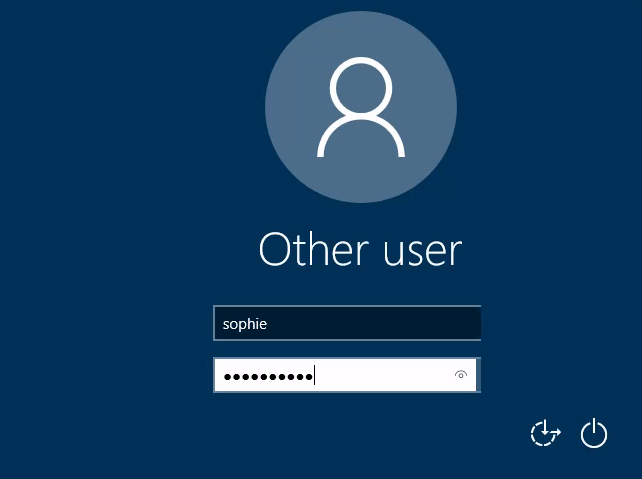

Now we have taken the flag. So we do not want Sophie to use our given password. We will force Sophie's account to show a reset option when Sophie will log into her account. The reset option showing process will be done from the Phillips account using this command: Set-ADUser -ChangePasswordAtLogon $true -Identity sophie -Verbose

Now see that you cannot enter Sophie’s account using the password you provided to get the flag. See that the password reset option has been shown.

The process of granting privileges to a user over some OU or other AD Object is called…
Answer: delegation
Note:
Your first task as the new domain administrator is to check the existing AD OUs and users, as some recent changes have happened to the business. You have been given the following organizational chart and are expected to make changes to the AD to match it:
Deleting extra OUs and users
The first thing you should notice is that there is an additional department OU in your current AD configuration that doesn’t appear in the chart. We’ve been told it was closed due to budget cuts and should be removed from the domain. If you try to right-click and delete the OU, you will get the following error:
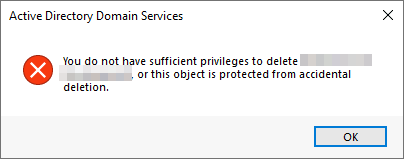
By default, OUs are protected against accidental deletion. To delete the OU, we need to enable the Advanced Features in the View menu:

This will show you some additional containers and enable you to disable the accidental deletion protection. To do so, right-click the OU and go to Properties. You will find a checkbox in the Object tab to disable the protection:

Be sure to uncheck the box and try deleting the OU again. You will be prompted to confirm that you want to delete the OU, and as a result, any users, groups, or OUs under it will also be deleted.
After deleting the extra OU, you should notice that for some of the departments, the users in the AD don’t match the ones in our organizational chart. Create and delete users as needed to match them.
Delegation (Example: A member of an IT support group can change the username and password of the other group's low-privilege members from his account because this power is given to him by the organization using the delegate control option of the target OU in the Active directory)
One of the nice things you can do in AD is to give specific users some control over some OUs. This process is known as delegation and allows you to grant users specific privileges to perform advanced tasks on OUs without needing a Domain Administrator to step in.
One of the most common use cases for this is granting IT support the privilege to reset other low-privilege users' passwords. According to our organizational chart, Phillip is in charge of IT support, so we'd probably want to delegate the control of resetting passwords over the Sales, Marketing, and Management OUs to him.
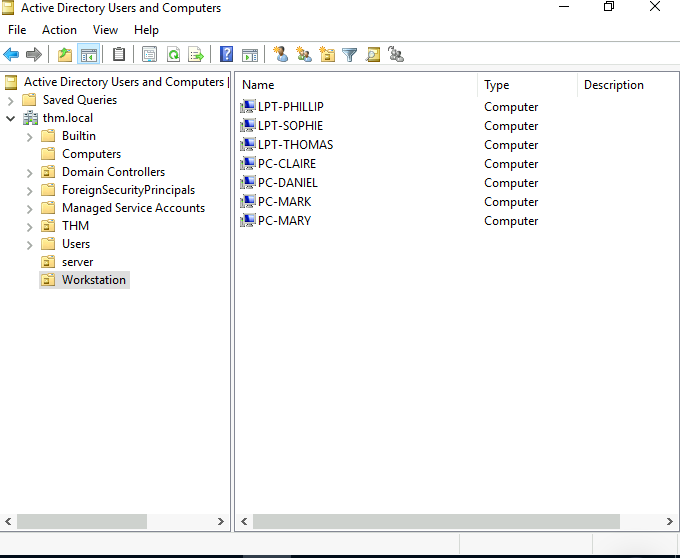
Task 5: Managing Computers in AD:
After organizing the available computers, how many ended up in the Workstations OU?
Answer: 7
Last updated